Hacking & Digital Arrest Scams – Cyber Crimes Decoded

Context:
- The United Nations General Assembly adopted a landmark cybercrime convention on December24, paving the way for significant changes to how governments police the internet.
- The Convention against Cybercrime was adopted without a vote and by consensus after a five-year negotiation.
- According to cyber cell data, Indians lost Rs 1,777 crore to cyber fraud in just the first four months of 2024. Of this, Rs 120 crore was lost to digital arrest scams.
- Digital arrest, among other scams, was highlighted by Prime Minister Narendra Modi during his monthly radio address 'Mann Ki Baat' on October 27, 2024.


1.
What is cybercrime?

- In general cybercrime may be defined as “Any unlawful act where a computer or communication device or computer network is used to commit or facilitate the commission of crime”.
- These crimes involve the use of technology to commit fraud, identity theft, data breaches, computer viruses, scams, and expanded upon in other malicious acts.
- Cybercrime is a serious issue in India, and the Information Technology Act (IT Act) of 2000 covers many types of cybercrimes.
2.
What is the history of cybercrime?
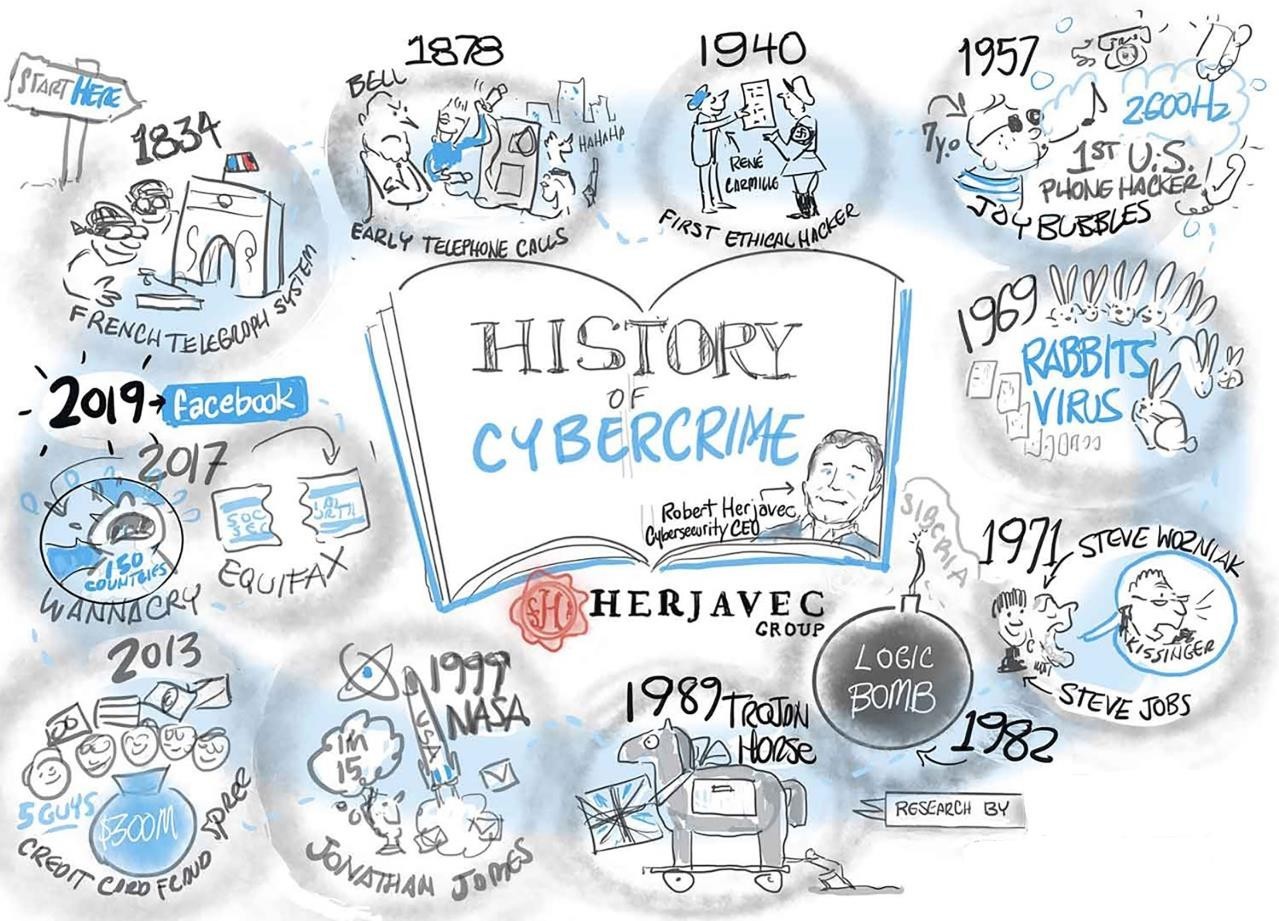
- The history of cybercrime can be traced back centuries, with the first recorded cyber attack in 1834 in France.
| Incident | Analysis |
|---|---|
| The telegraph system |
|
| The telephone system |
|
| Ethical hacking |
|
| Phishing scams and malware |
|
| Social media scams |
|
| First conviction |
|
3.
What is the UN cybercrime treaty?

- The UN Convention against Cybercrime aims to prevent and combat cybercrime more efficiently and effectively, including by strengthening international cooperation and by providing technical assistance and capacity-building support, particularly for developing countries.
- The adoption of this landmark convention is a major victory for multilateralism, marking the first binding international anti-crime treaty in 20 years.
- The UN Office on Drugs and Crime (UNODC) served as secretariat to the negotiations.
- The General Assembly adopted the resolution without a vote.
- The Convention will open for signature at a formal ceremony to be hosted by VietNam in 2025 and will enter into force 90 days after being ratified by the 40th signatory.
4.
Enlist various types of cybercrimes?
| Types of cybercrimes | Analysis |
|---|---|
| Child Pornography/ Child sexually abusive material (CSAM) |
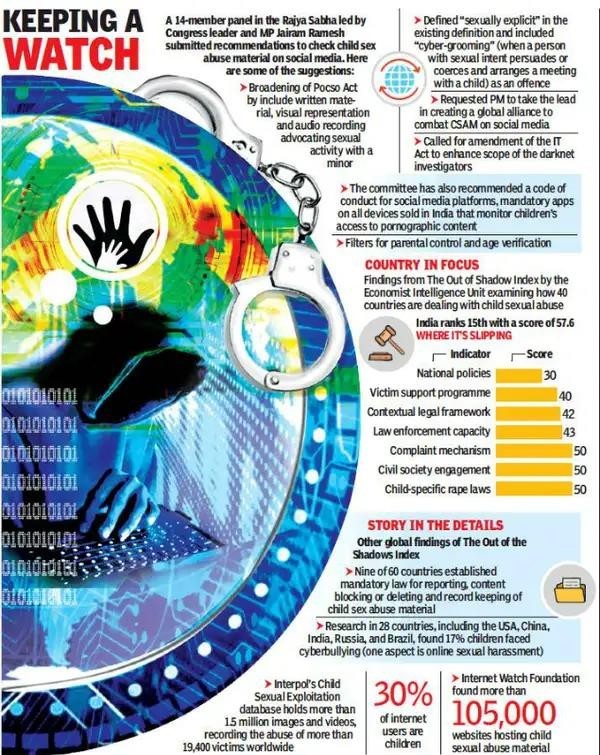 |
| Cyber Bullying |

|
| Cyber stalking |
 |
| Online Job Fraud |
 |
| Online Sextortion |
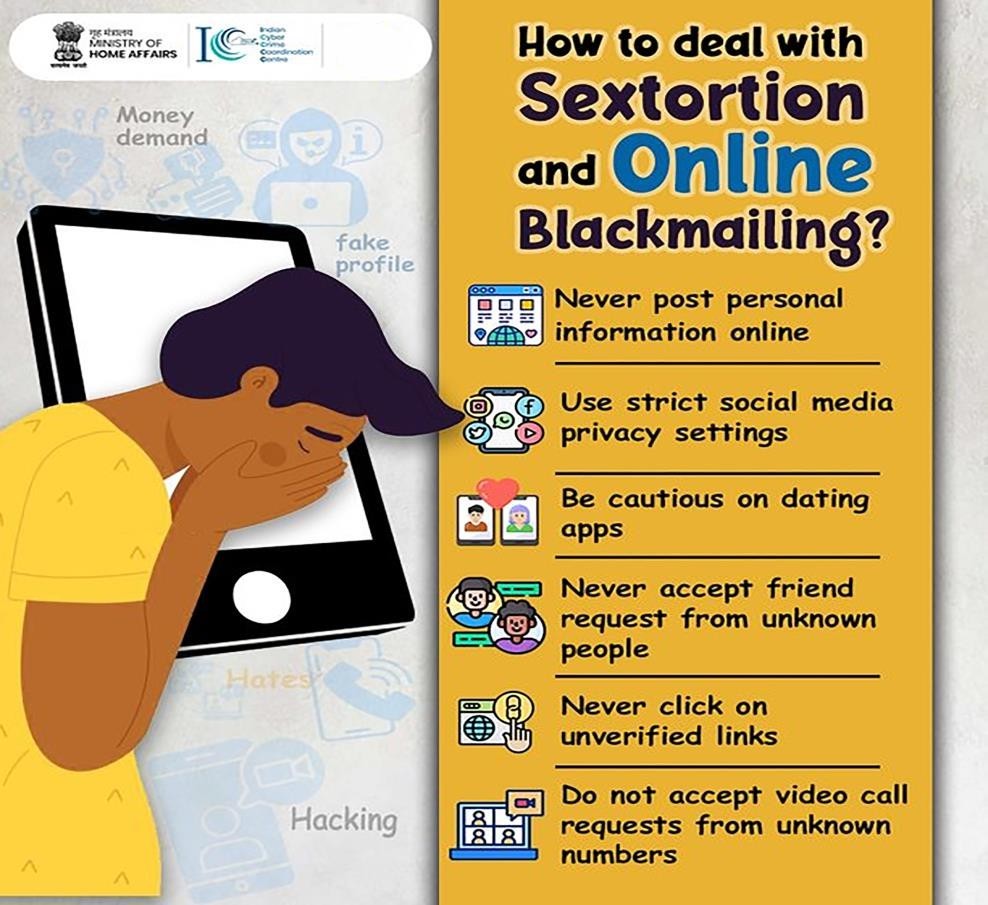 |
| SIM Swap Scam |
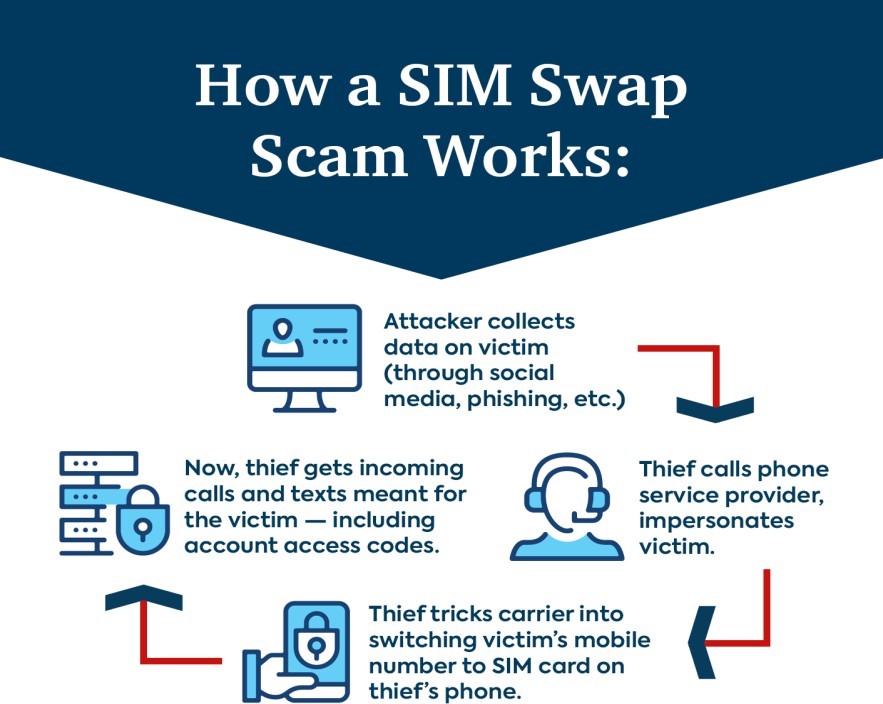 |
| Phishing |
 |
| Denial Of Services /Distributed DoS |
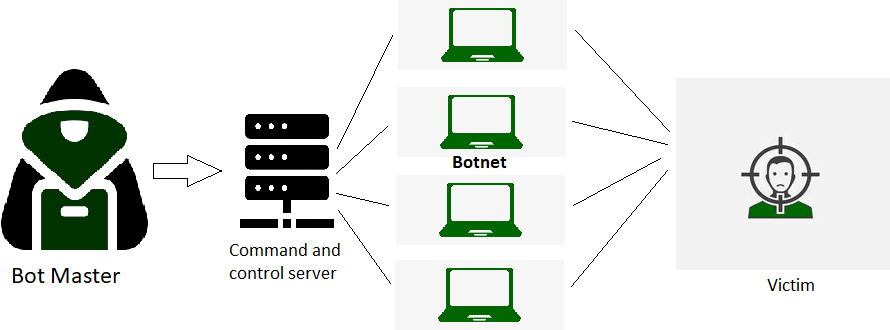 |
| Spamming |
 |
| Espionage |
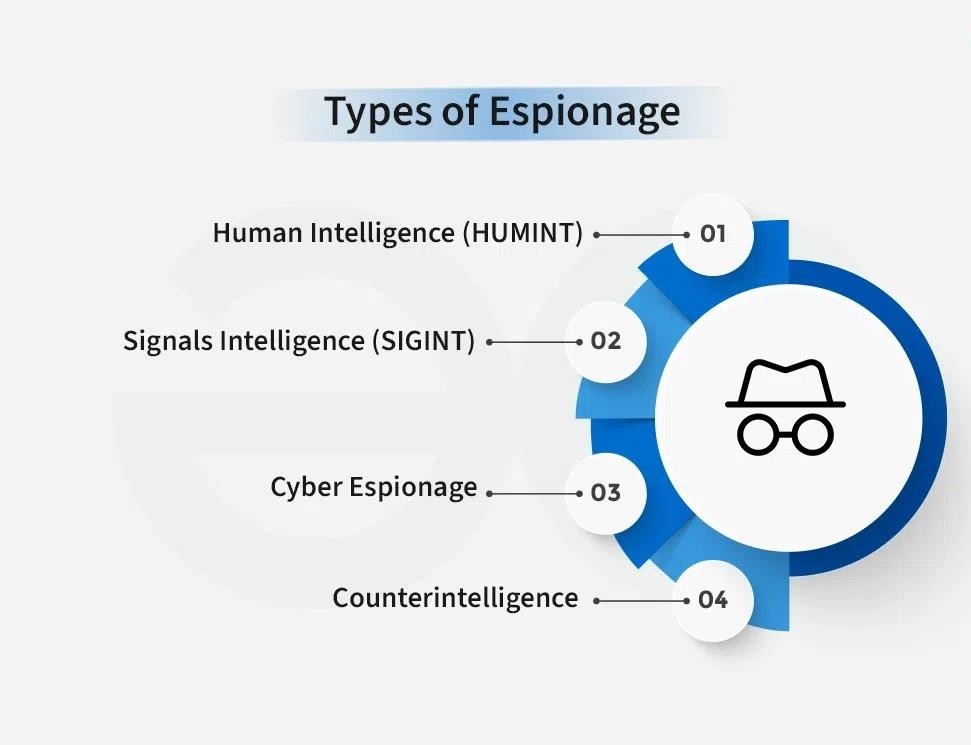 |
| Cryptojacking |
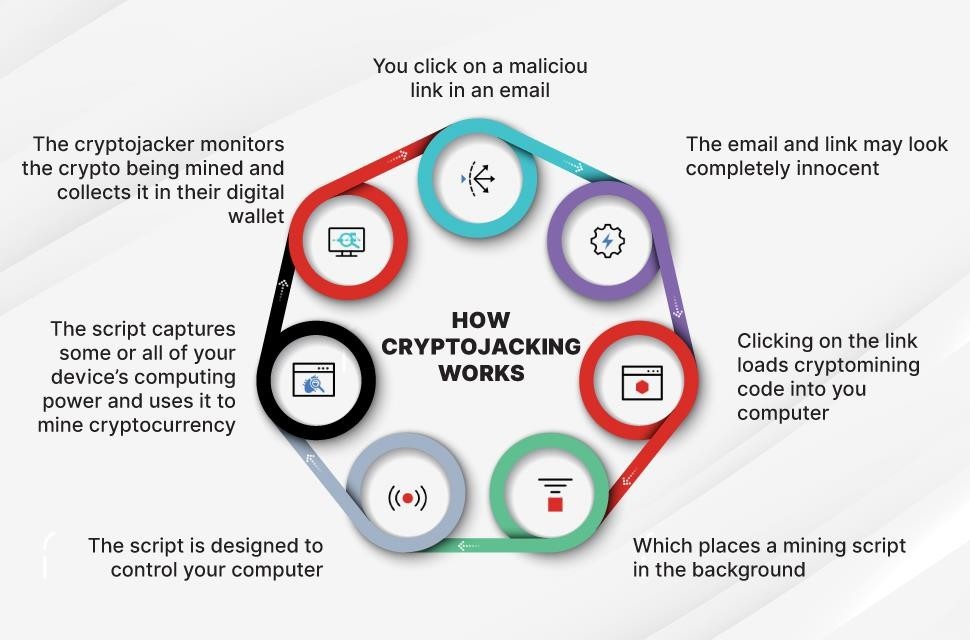 |
5.
Enlist a range of cybercrimes against the government?

| Cybercrime | Analysis |
|---|---|
| Cyber Terrorism |
|
| Cyber Warfare |
 |
| Distribution of pirated software |
|
| Possession of Unauthorized Information |
|
6.
What is Hacking and enlist its types?
- Hacking in cyber security refers to the misuse of devices like computers, smartphones, tablets, and networks to cause damage to or corrupt systems, gather information on users, steal data and documents, or disrupt data-related activity
- Hacking first appeared as a term in the 1970s but became more popular through the next decade.
- Hacking can be of following types:
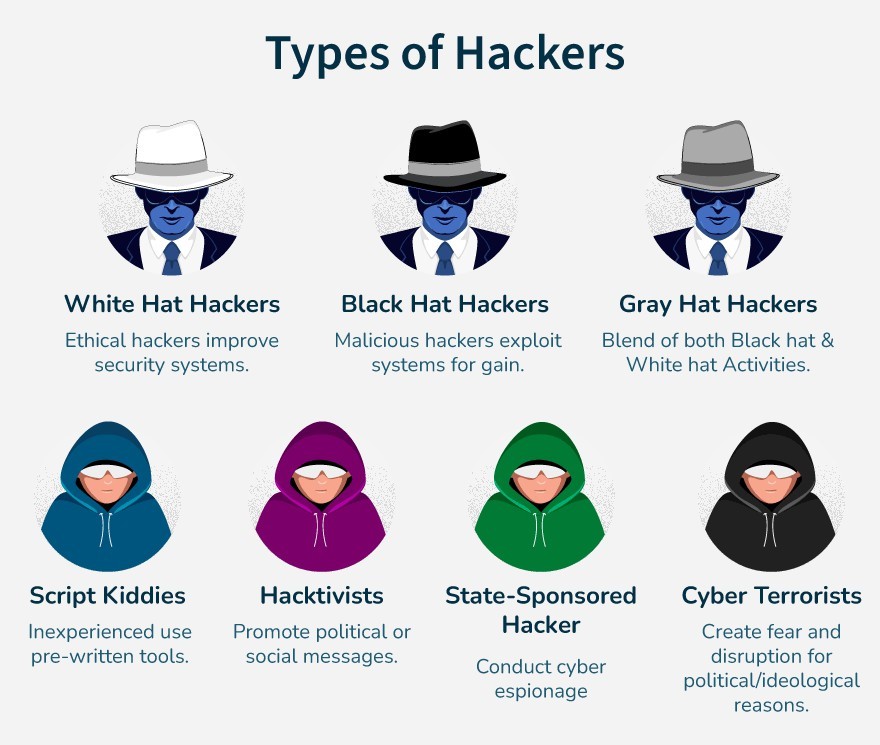
| Types of Hacking | Description |
|---|---|
| Black hat hackers |
 |
| White hat hackers |
 |
| Grey hat hackers |
|
7.
What is malware and mention its types?
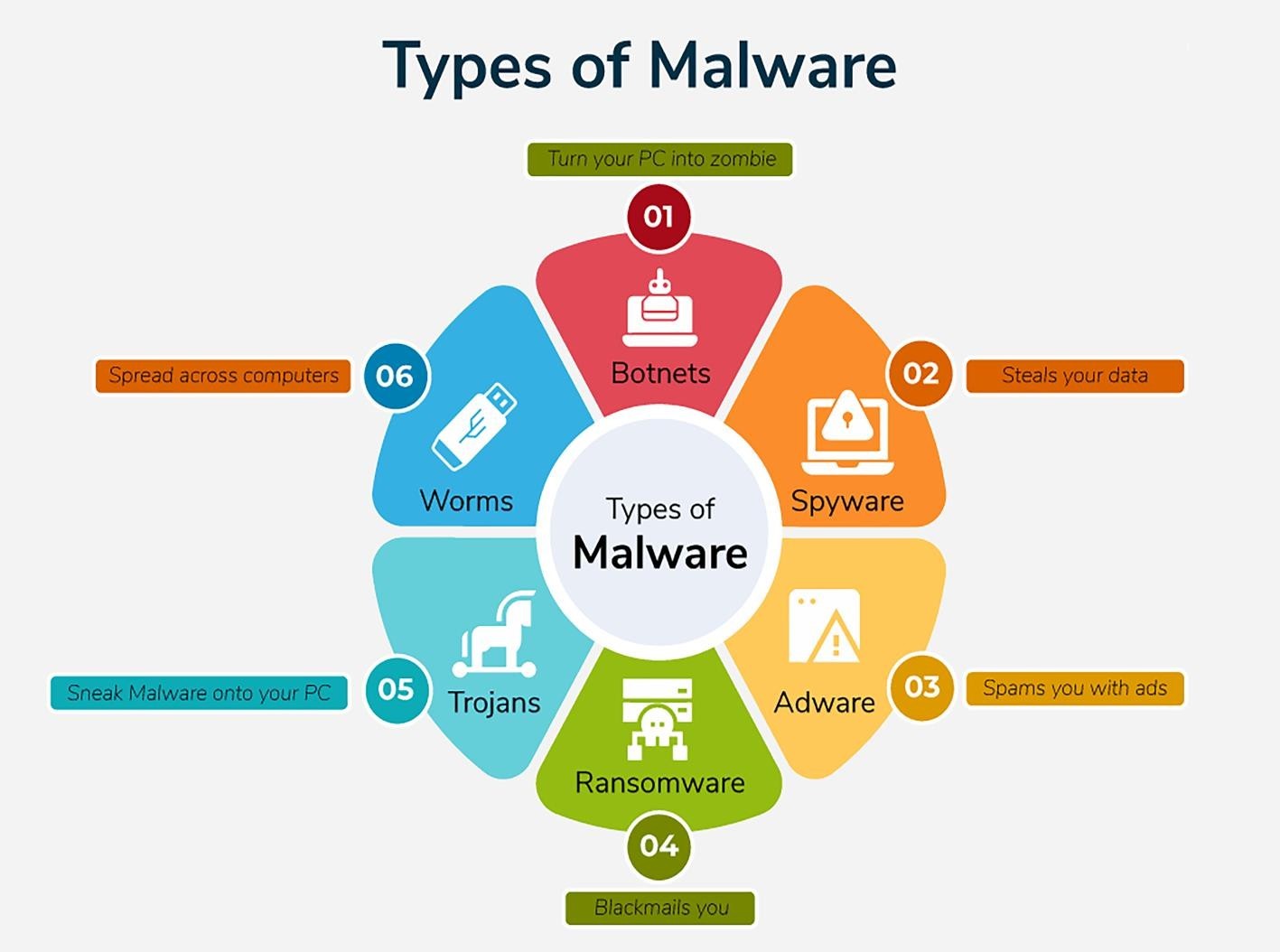
- Malware is malicious software that a cybercriminal/hacker creates to disrupt/damage computer/s or derive financial benefits.
- It is often spread by way of an unsolicited email attachment or download link.
- They can be of following types:
| Types of Malware | Analysis |
|---|---|
| Virus |
|
| Trojans |
|
| Spyware |
|
| Ransomware |
|
| Adware |
|
| Logic Bombs |
 |
| Keyloggers |
 |
| Backdoors |
|
8.
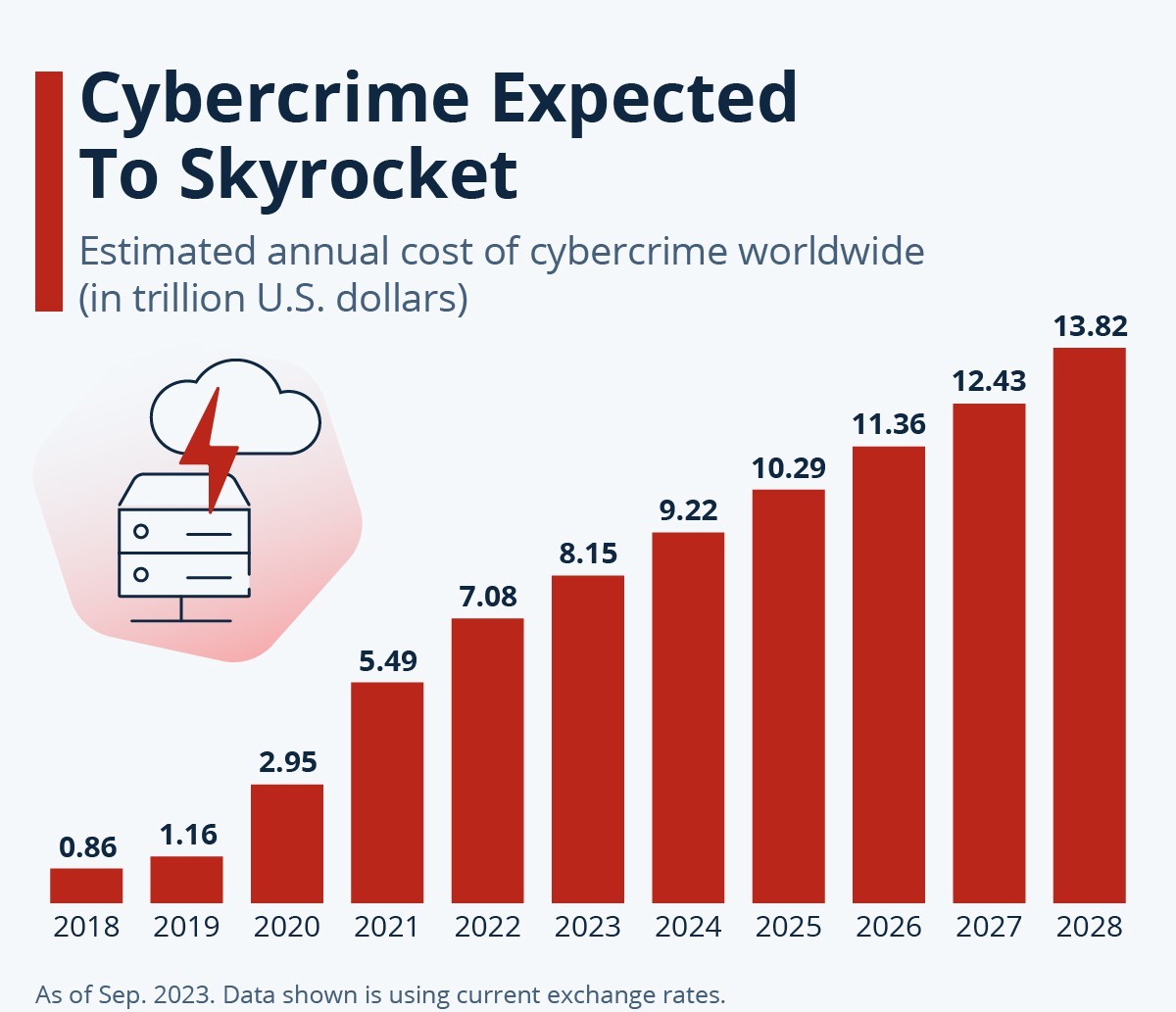
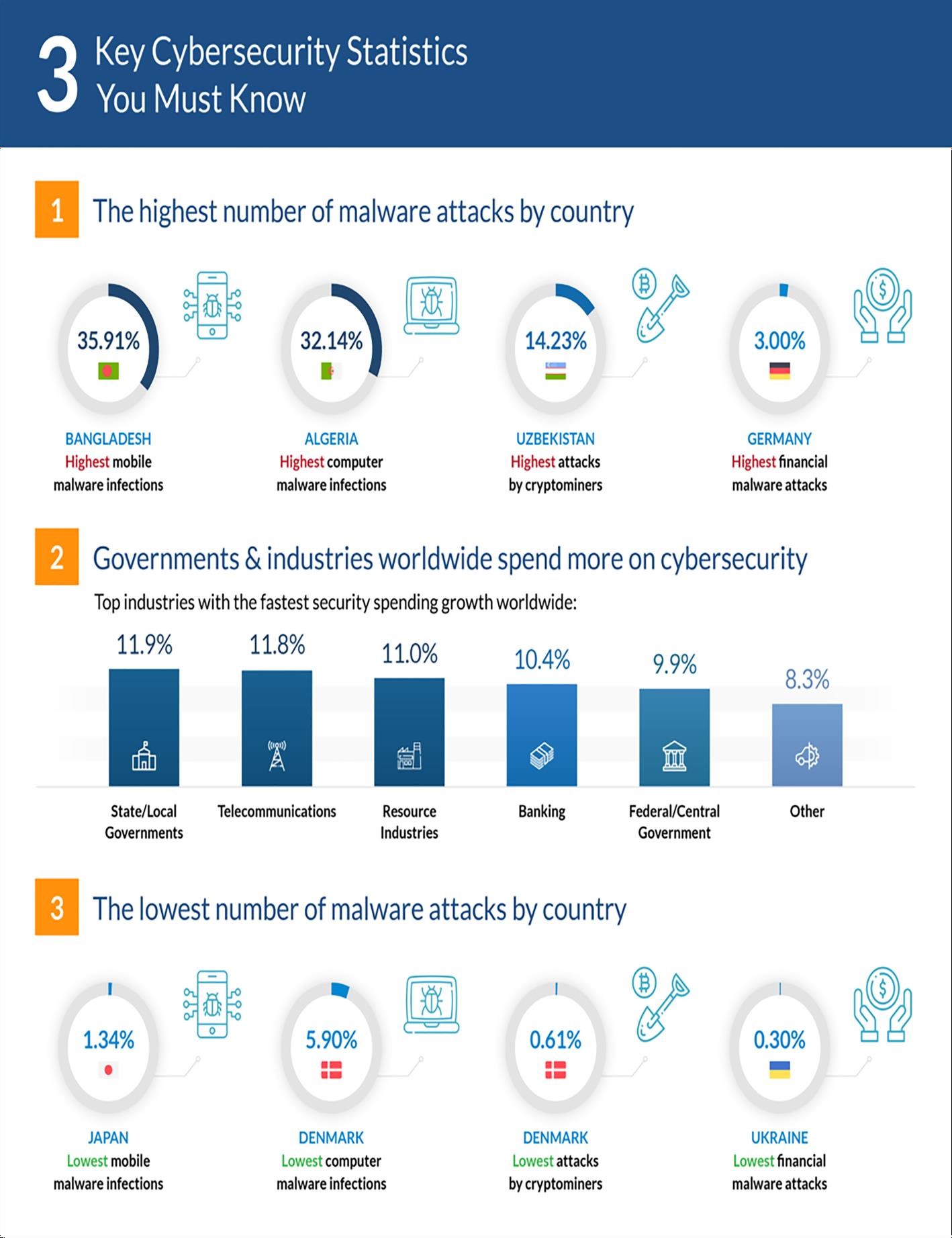
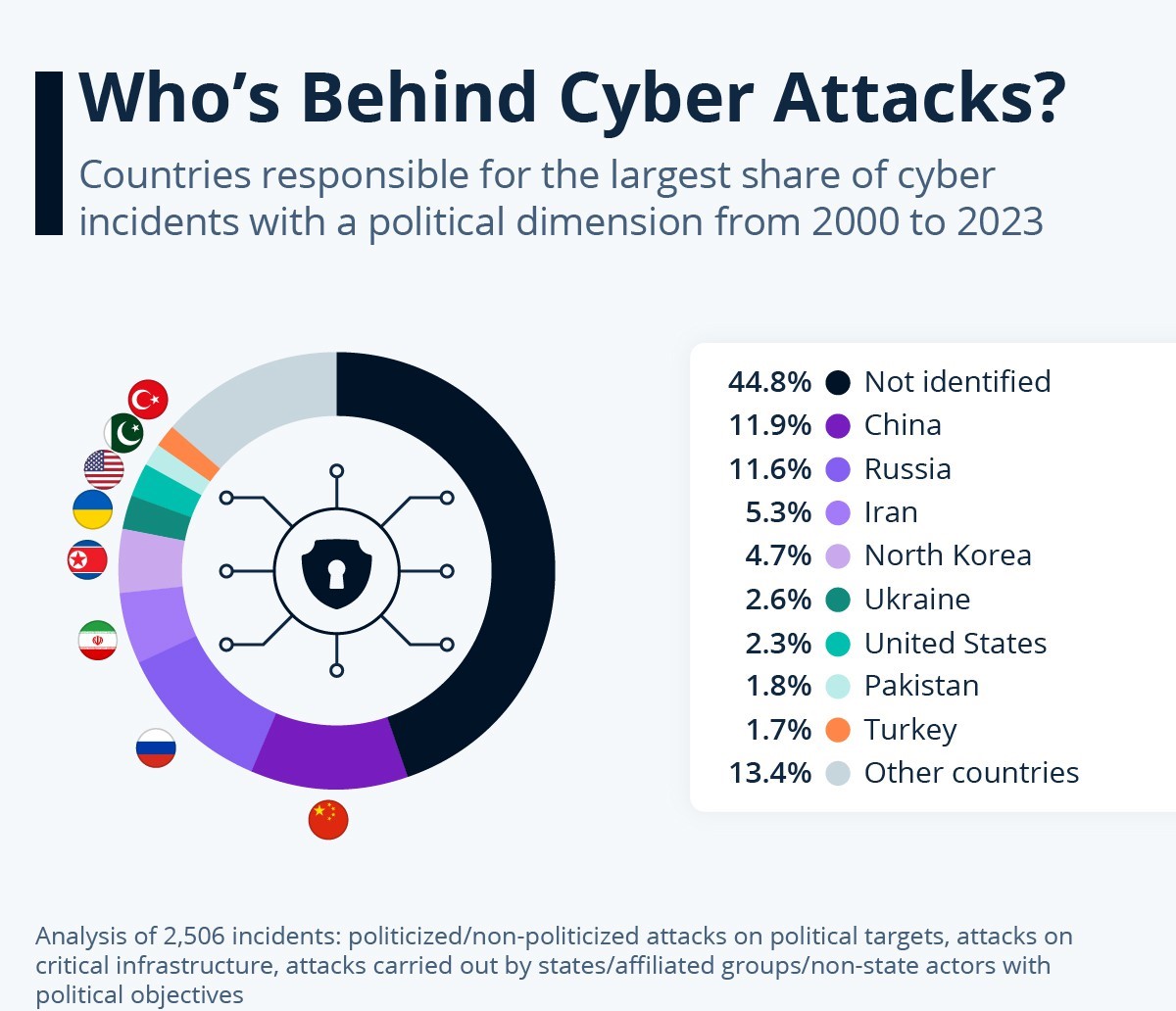
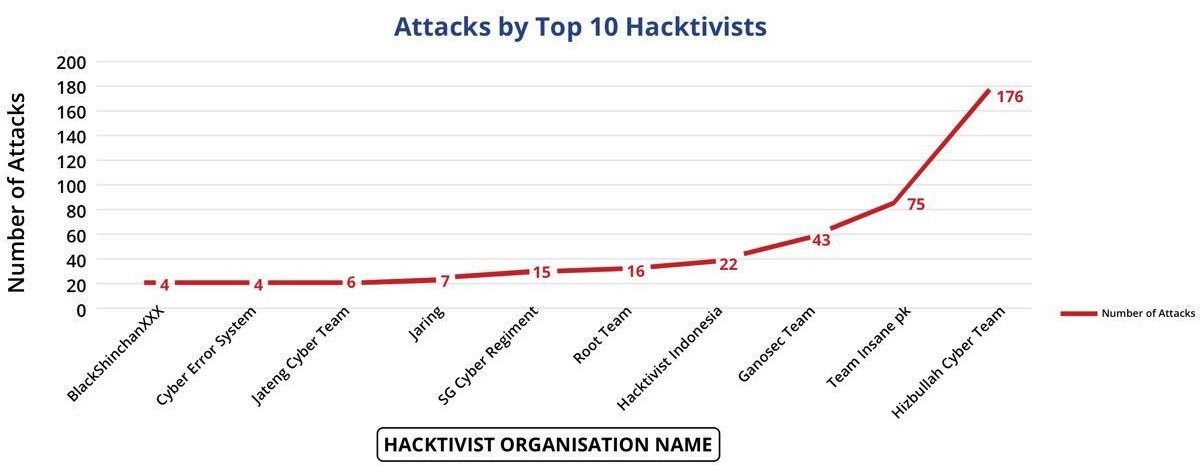
Enlist data on global cyberattacks?
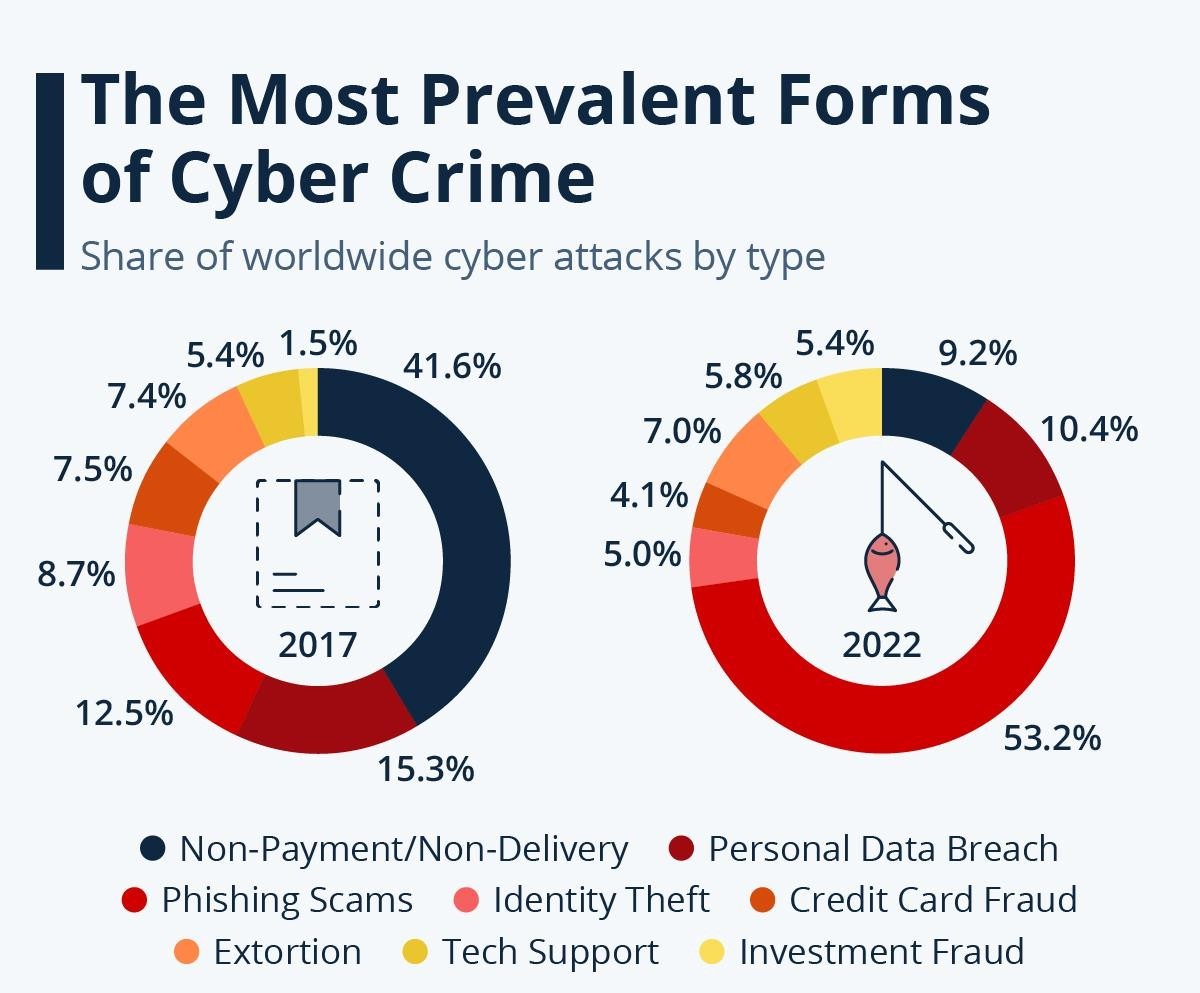
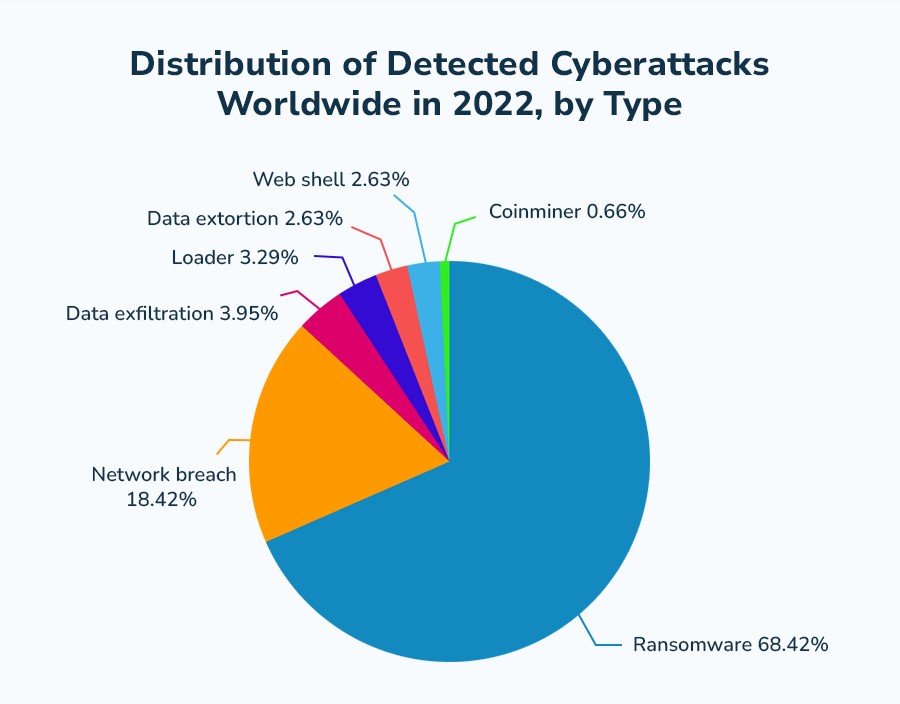
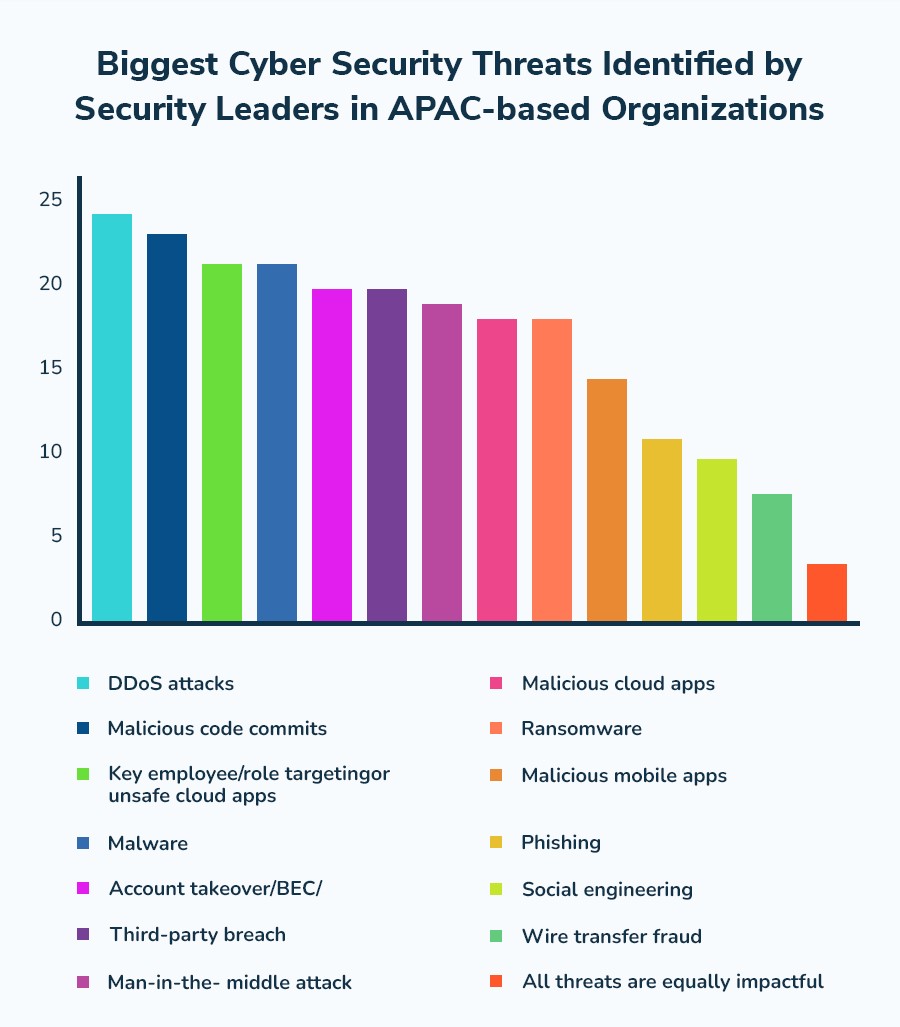
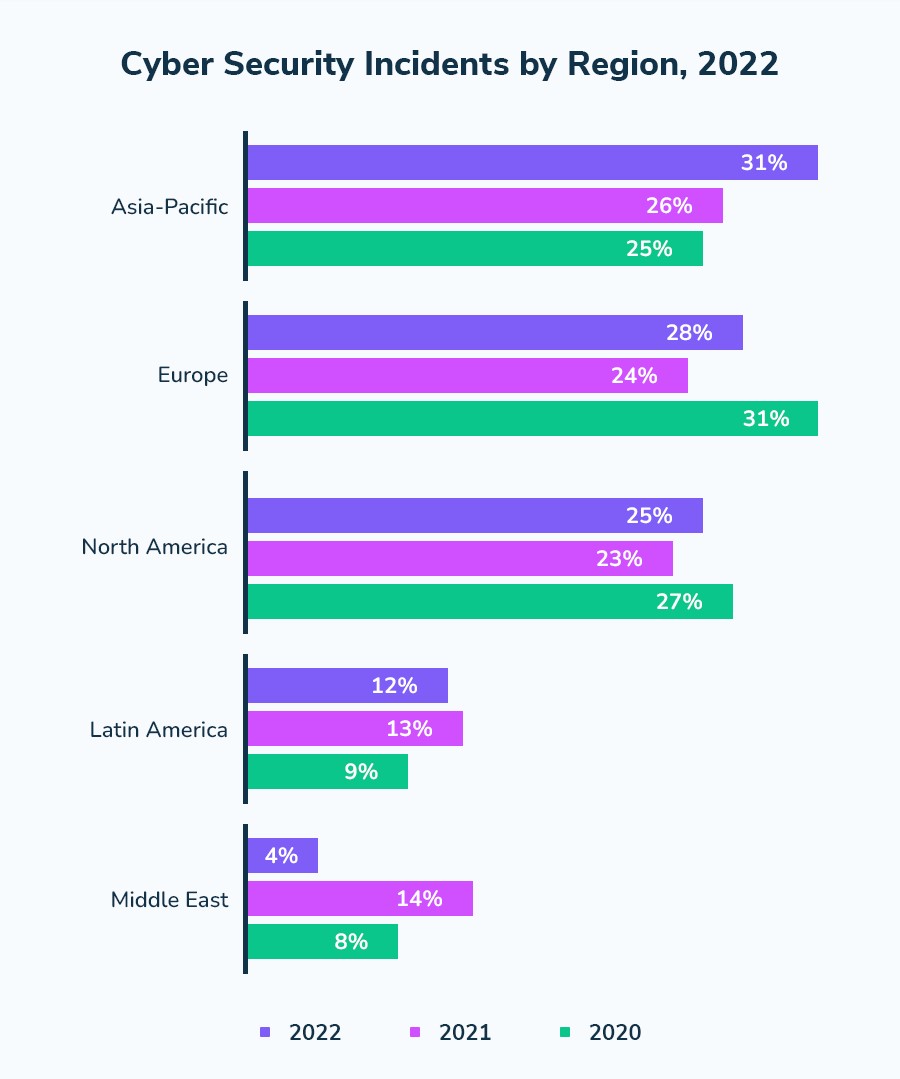
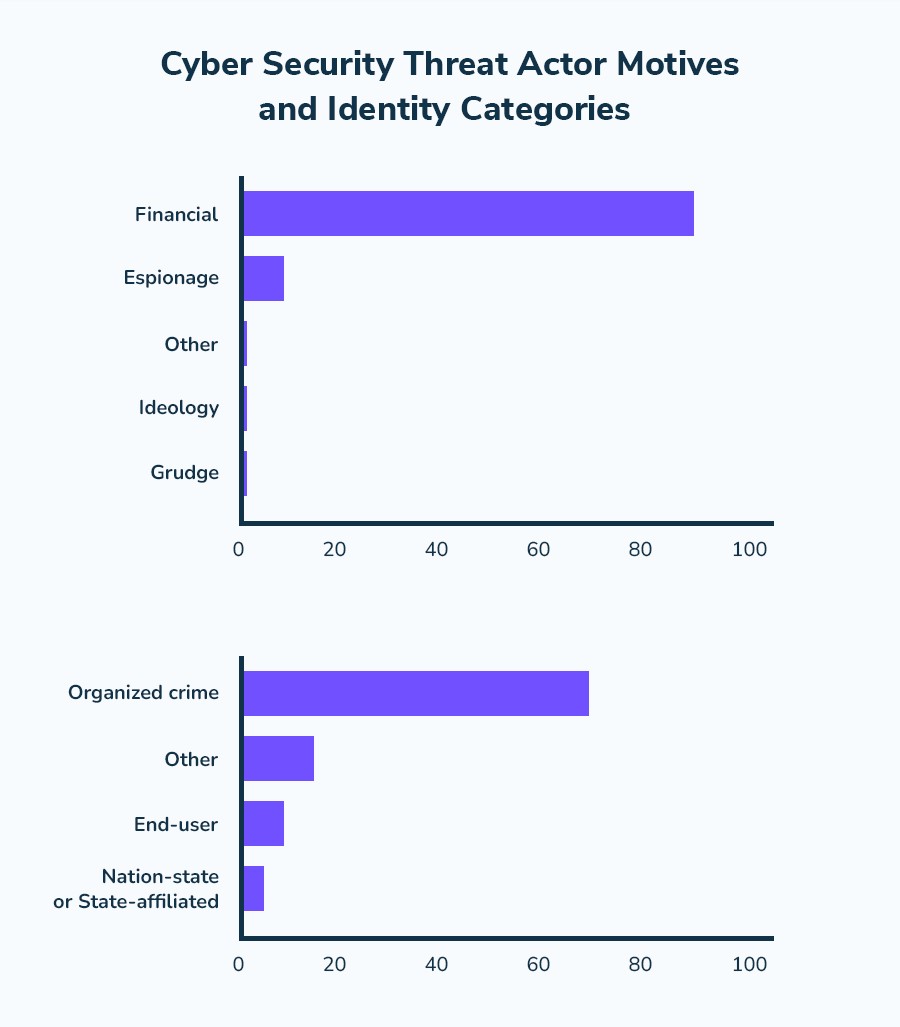
9.
What is Digital Arrest?
- Digital Arrest is a new and innovative tactic employed by cybercriminals to defraud gullible victims and extort money.
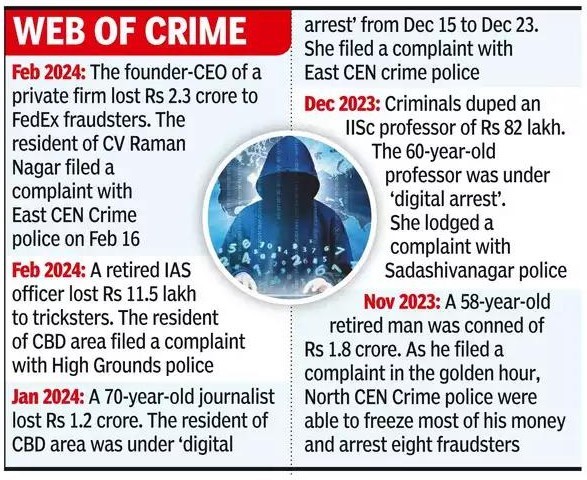
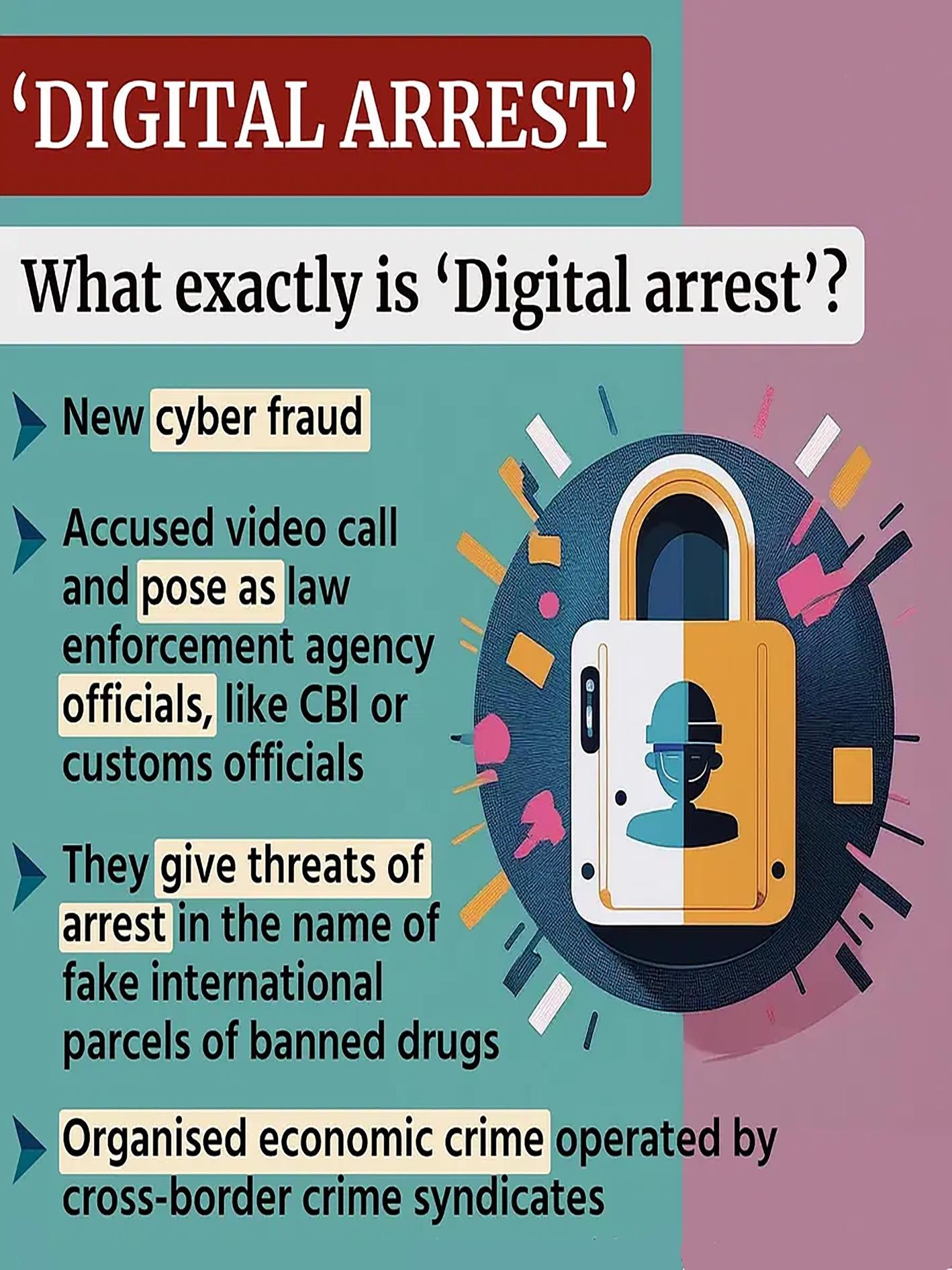




10.
What is the status of cybercrime in India?
- India was placed on the 80th position in a report focusing on local threats in the year 2023.
- The position is based on the malicious programmes found directly on users‟ computers or removable media connected to them (flash drives, camera memory cards, phones, external hard drives) or that initially made their way onto the computer in non-open form, including programmes in complex installers or encrypted files.
- Additionally, nearly 34% of users in India were targeted by local threats, amounting to some 74,385,324 local incidents being blocked by Kasperksy products.
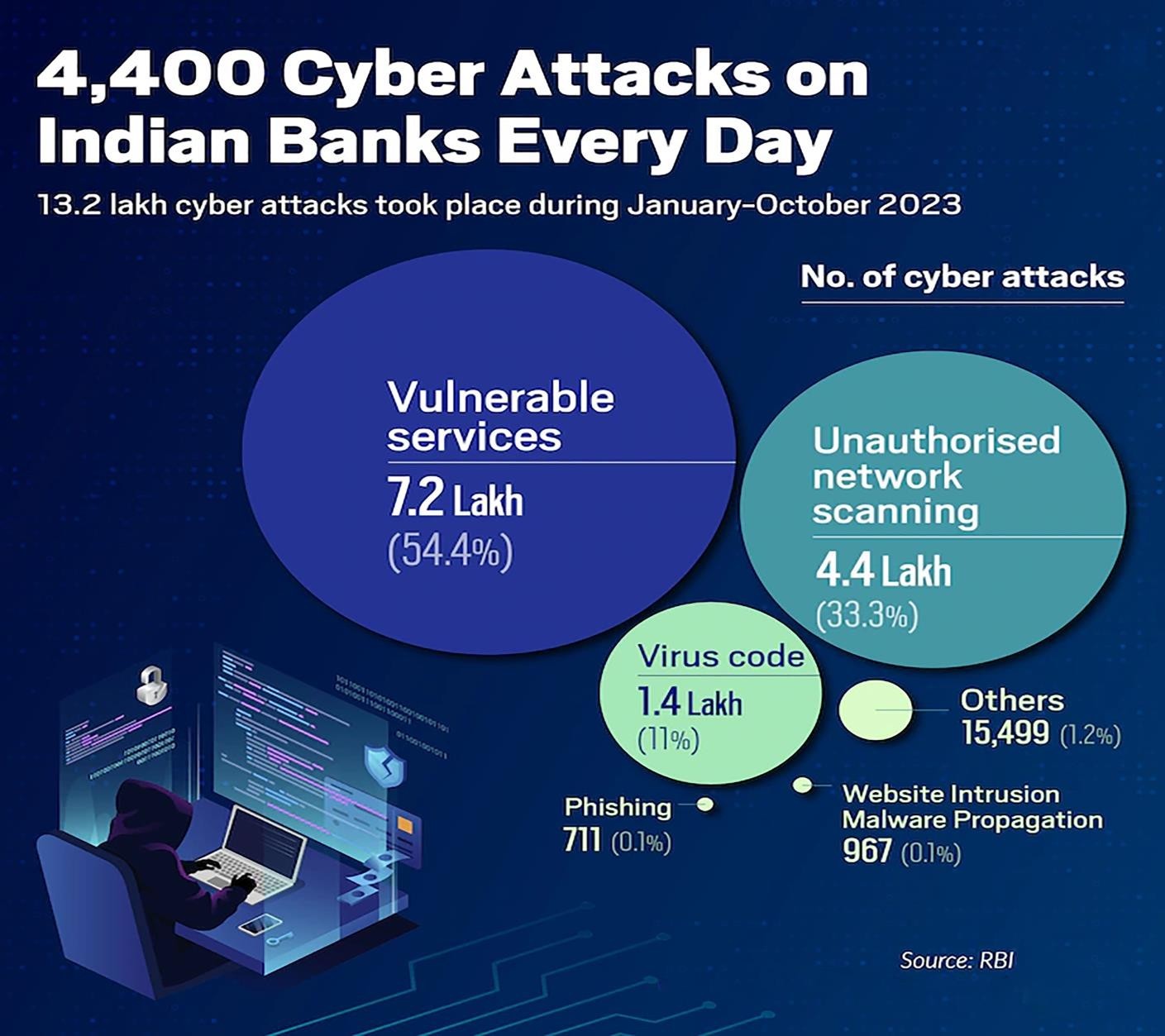
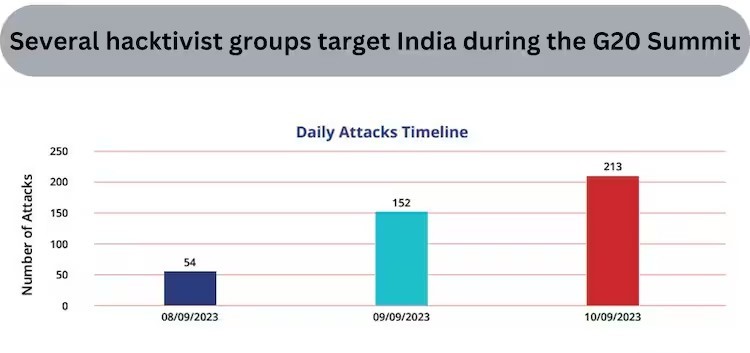

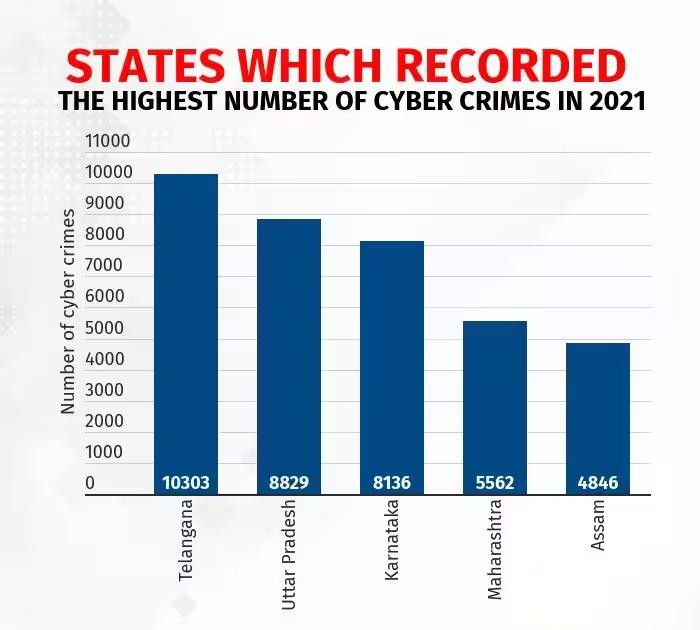
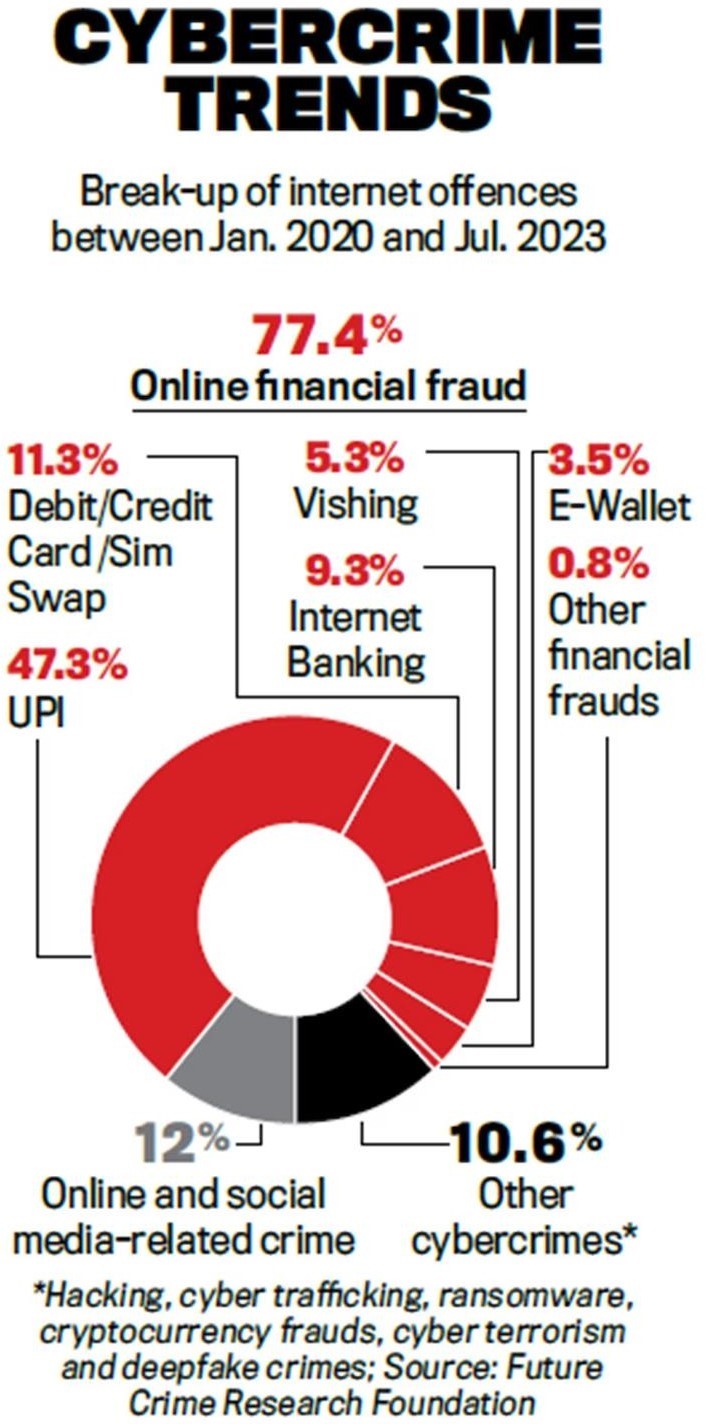

11.
Enlist the findings of the India Cyber Threat Report 2023?
- The India cyber threat report 2023 is released by the Data Security Council of India (DSCI) and Quick heal.
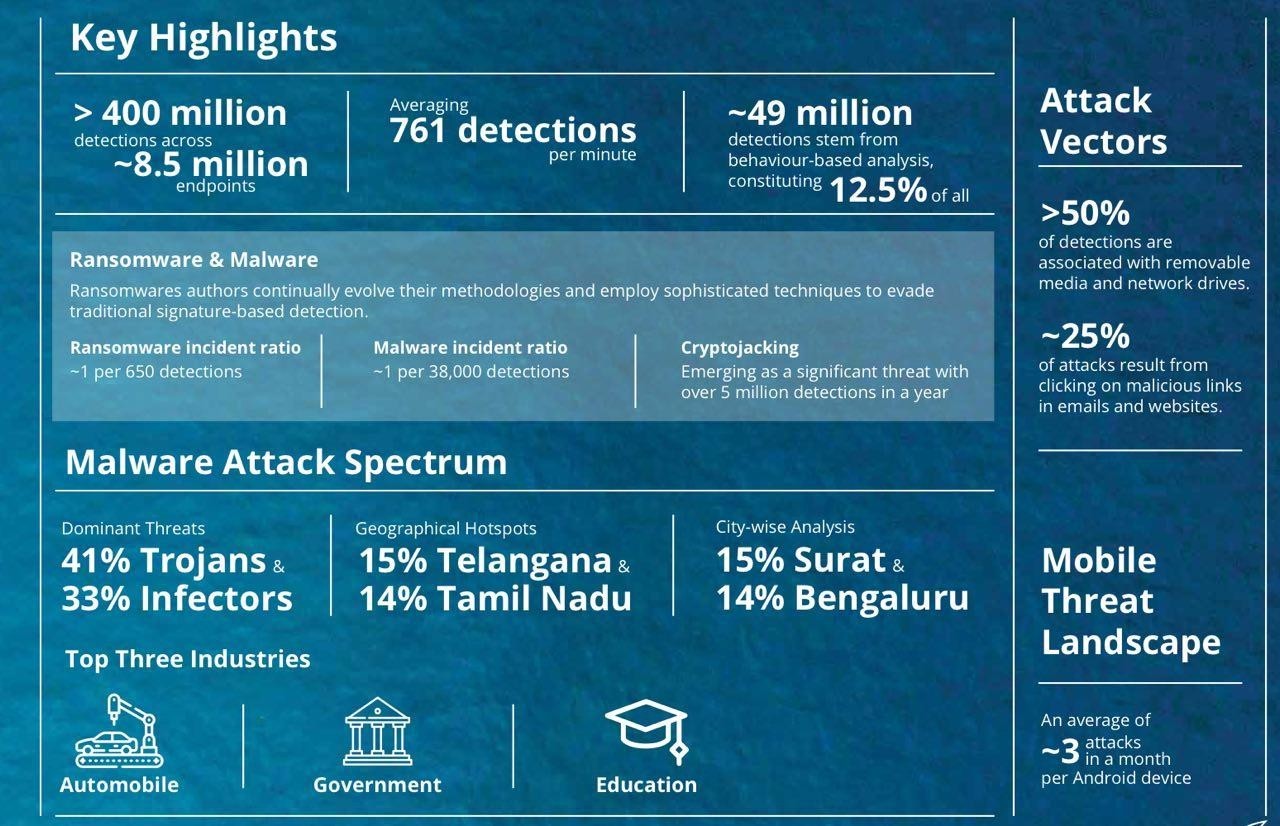
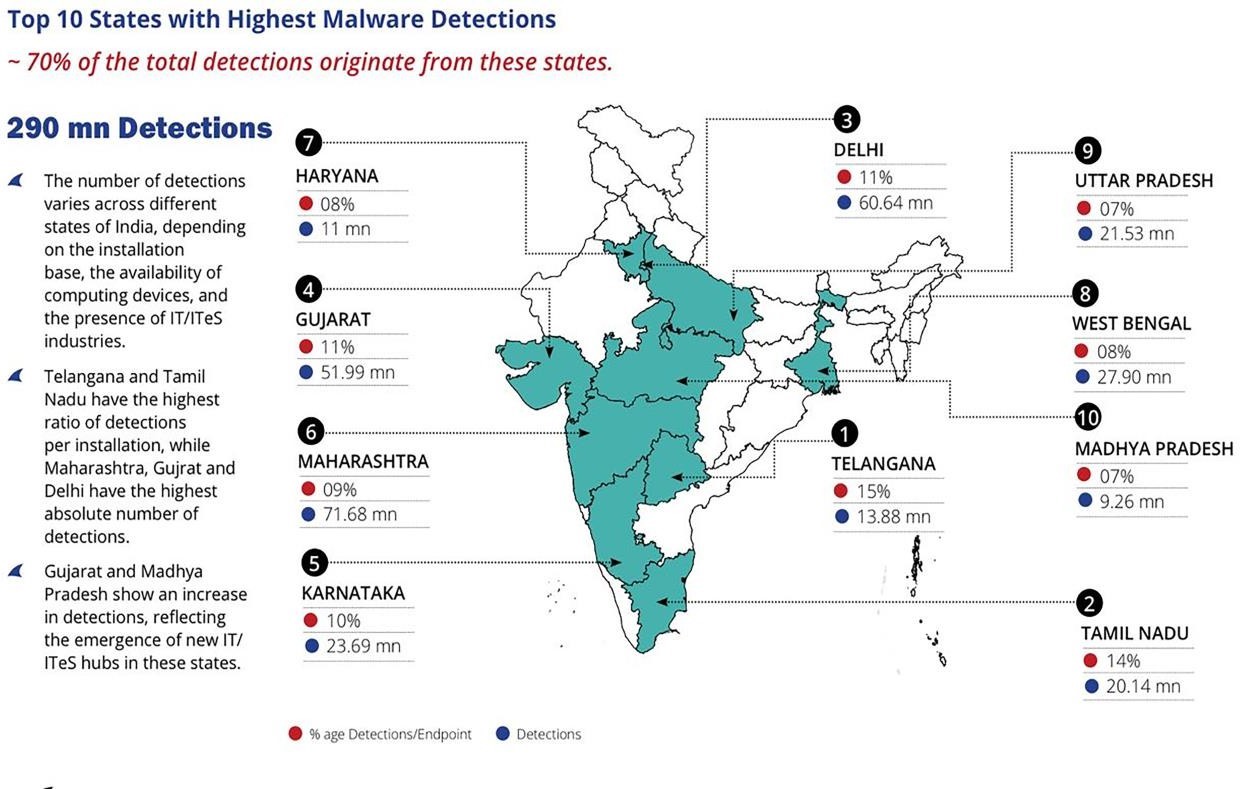
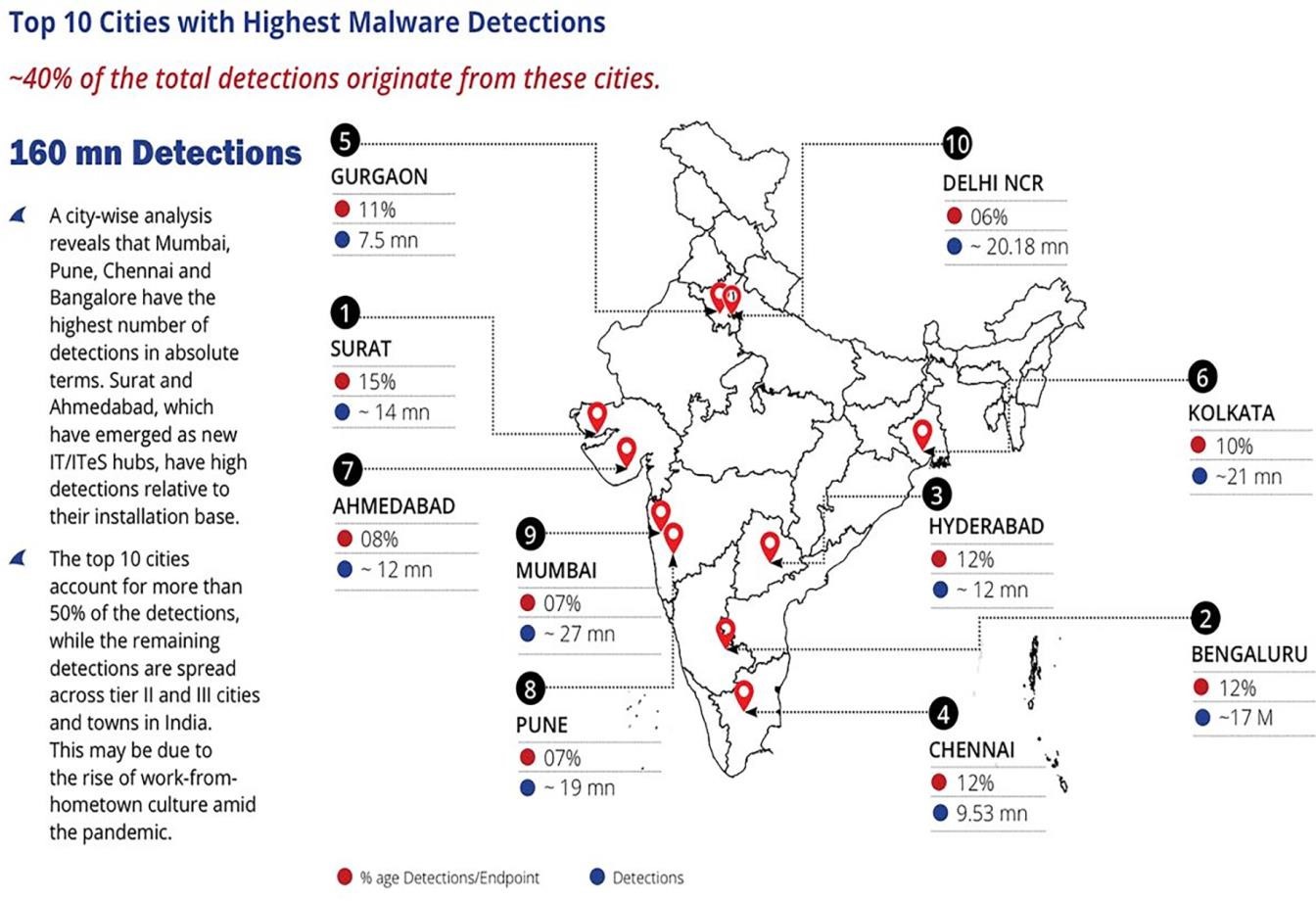
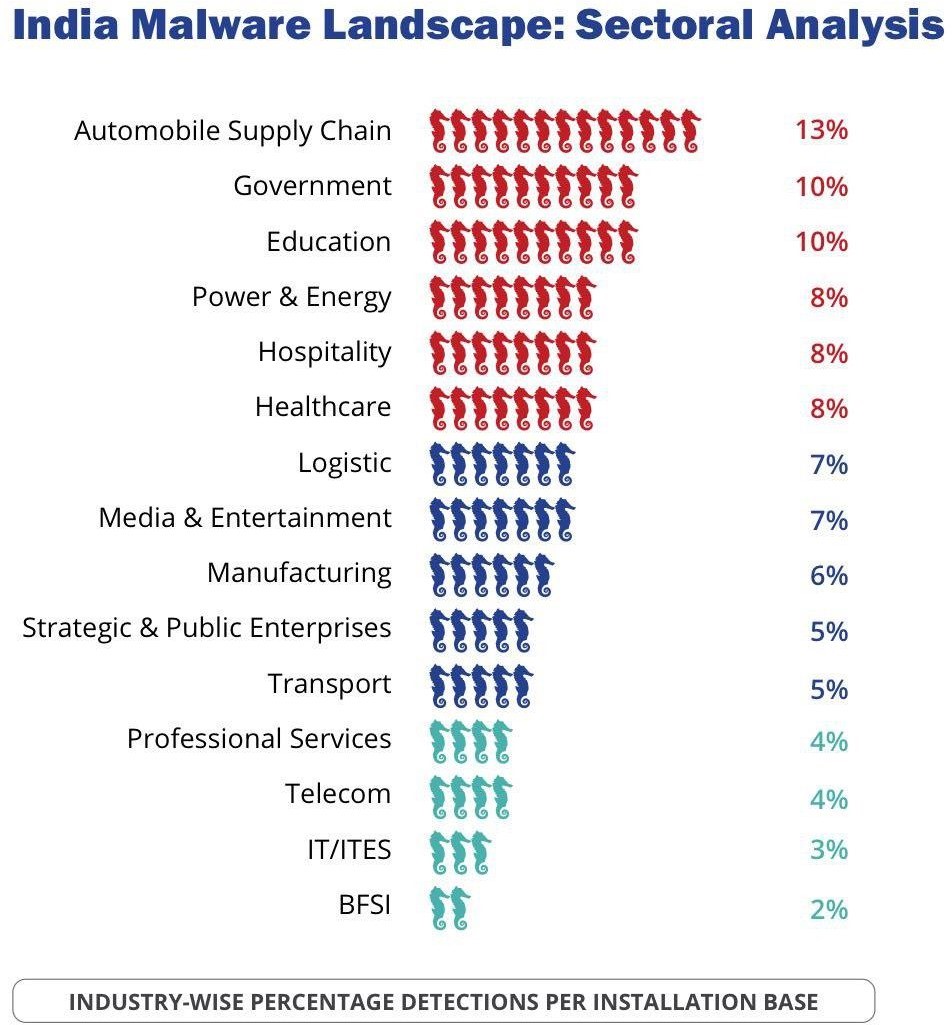
12.
What are the reasons for rising cyber crimes in India?

- The rise of cybercrime in India is a complex issue, with several key factors contributing to its growth and impact.
- Here are the few important reasons for the rise of cybercrime in India.
| Reasons | Analysis |
|---|---|
| Increasing Internet Penetration |
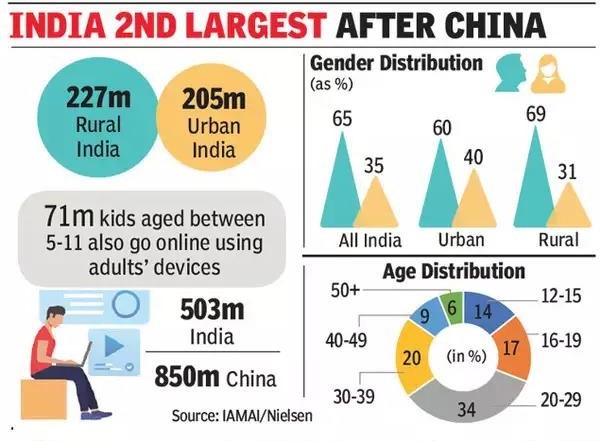 |
| Rapid Digital Transformation |
 |
| Financial Incentives |
|
| Lack of Cybersecurity Awareness |
|
| Data Privacy Concerns |
|
| Lack of cyber hygiene |
 |

13.
Mention about the epicenter of cybercrimes in India?
- According to a 2023 report, „A Deep Dive into Cybercrime Trends Impacting India‟ by the Future Crime Research Foundation, an IIT Kanpur incubated start-up, among the top 10 cybercrime epicentres are Bharatpur – Rajasthan (18%), Mathura – Uttar Pradesh (12%), Nuh – Haryana (11%), Deoghar – Jharkhand (10%) and Jamtara – Jharkhand (9.6%).
- The report said several common factors contribute to their vulnerability, including geographical proximity to major urban centers, limited cybersecurity infrastructure, socioeconomic challenges, and low digital literacy.
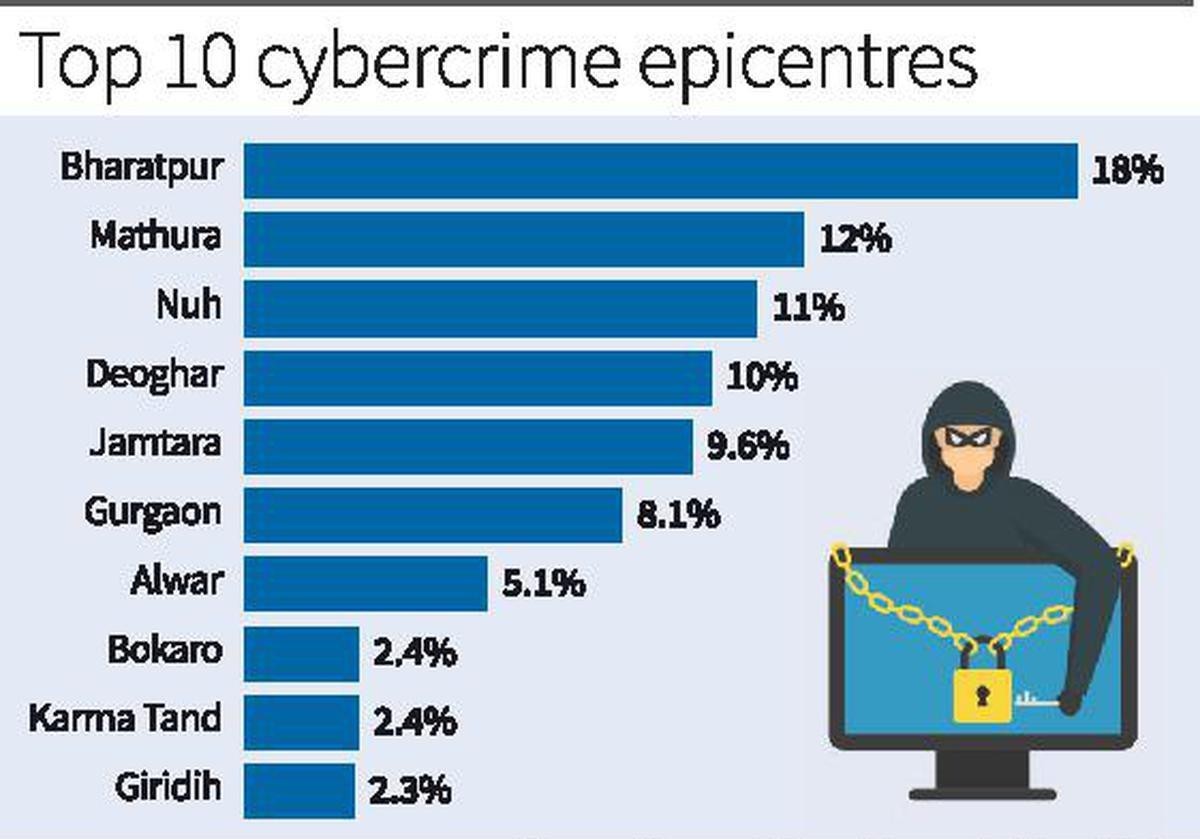
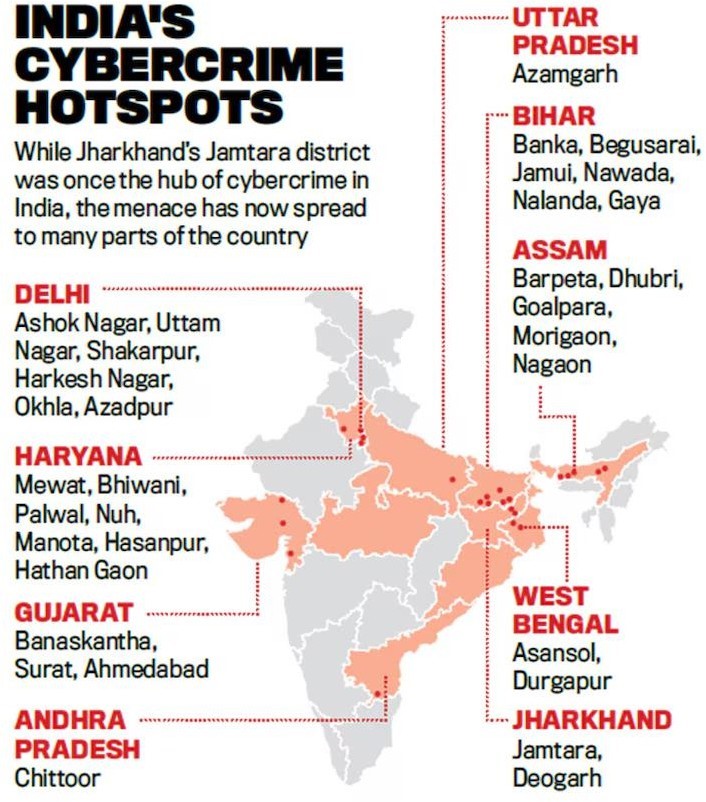
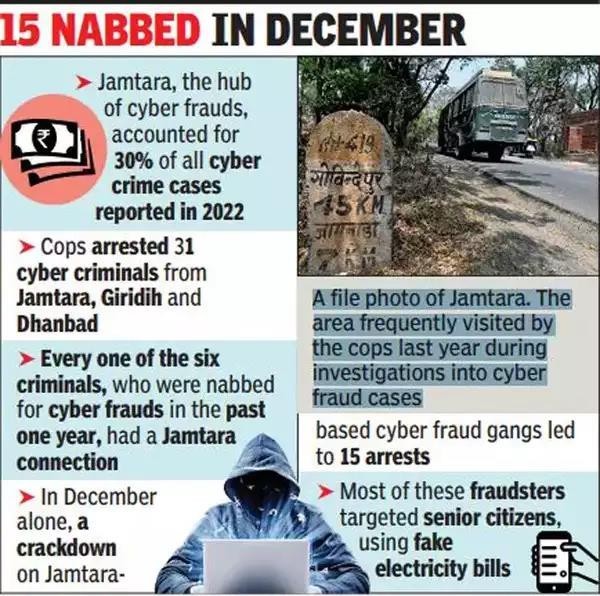
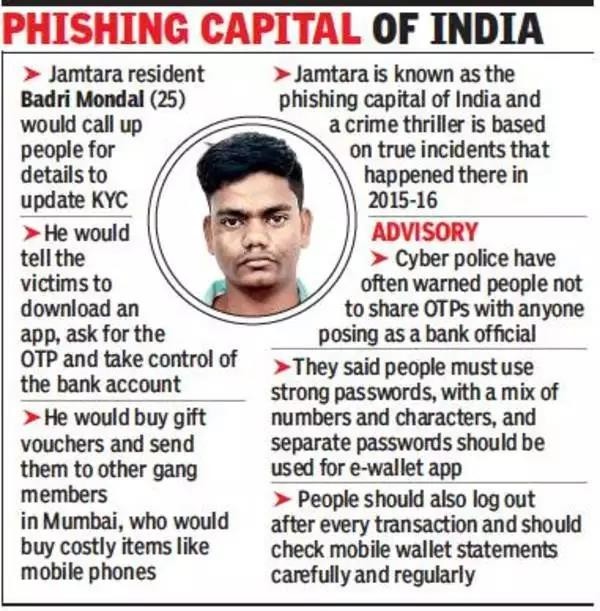
14.
What are the impacts of cybercrime in India?
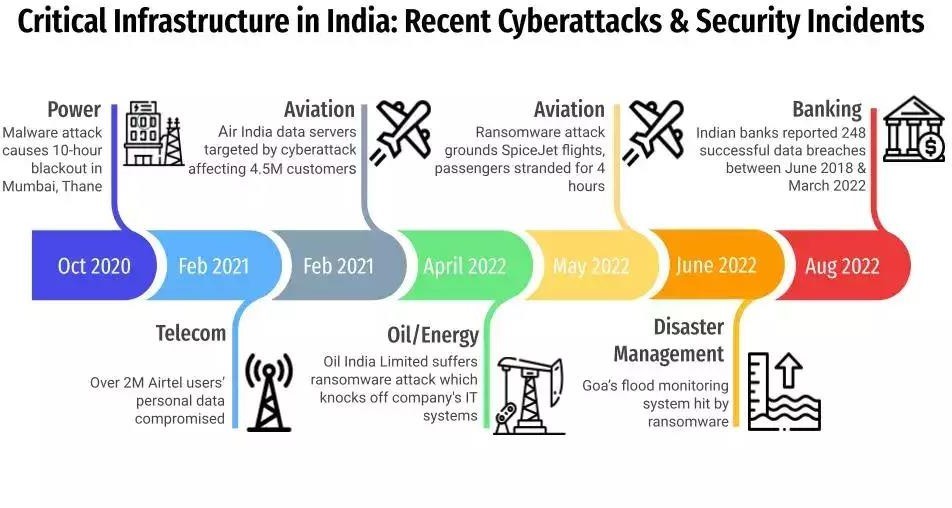
| Impacts | Analysis |
|---|---|
| Financial Losses |
|
| Data Breaches and Privacy Concerns |
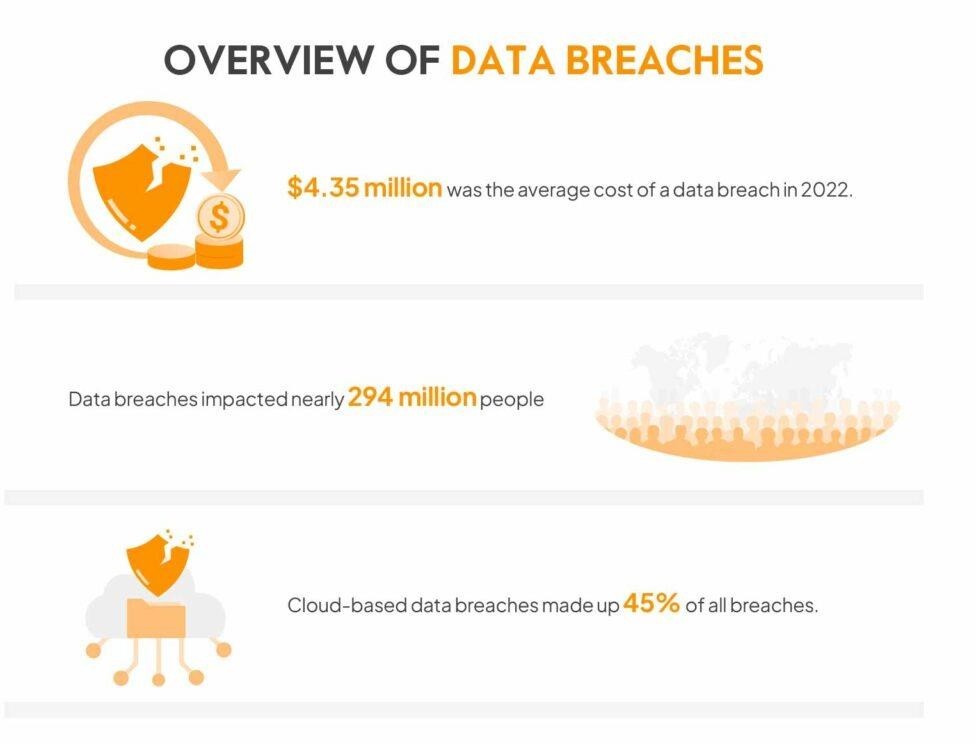 |
| Disruption of Critical Infrastructure |
|
| Social and Psychological Impact |
|
15.
Enlist global measures to tackle cybercrime?
| Measure | Analysis |
|---|---|
| Interpol Cybercrime Global Strategy 2022- 2025: |
 |
| Potential UN Cybercrime Treaty |
|
| Budapest Convention |
 |
16.
Enlist measures taken by the Government of India to combat cybercrime in India?
| Measure | Analysis |
|---|---|
| Indian Cyber Crime Coordination Centre (I4C) |
 |
| National Cyber Forensic Laboratory |
 |
| CyTrain Porta |
 |
| National Cyber Crime Reporting Portal |
 |
| Information Technology (IT) Act, 2000 |
 |
| Citizen Financial Cyber Fraud Reporting and Management System |
|
| Cybercrime Prevention against Women and Children (CCPWC) Scheme |
 |
| Central Assistance for Modernizatio n of Police |
 |
17.
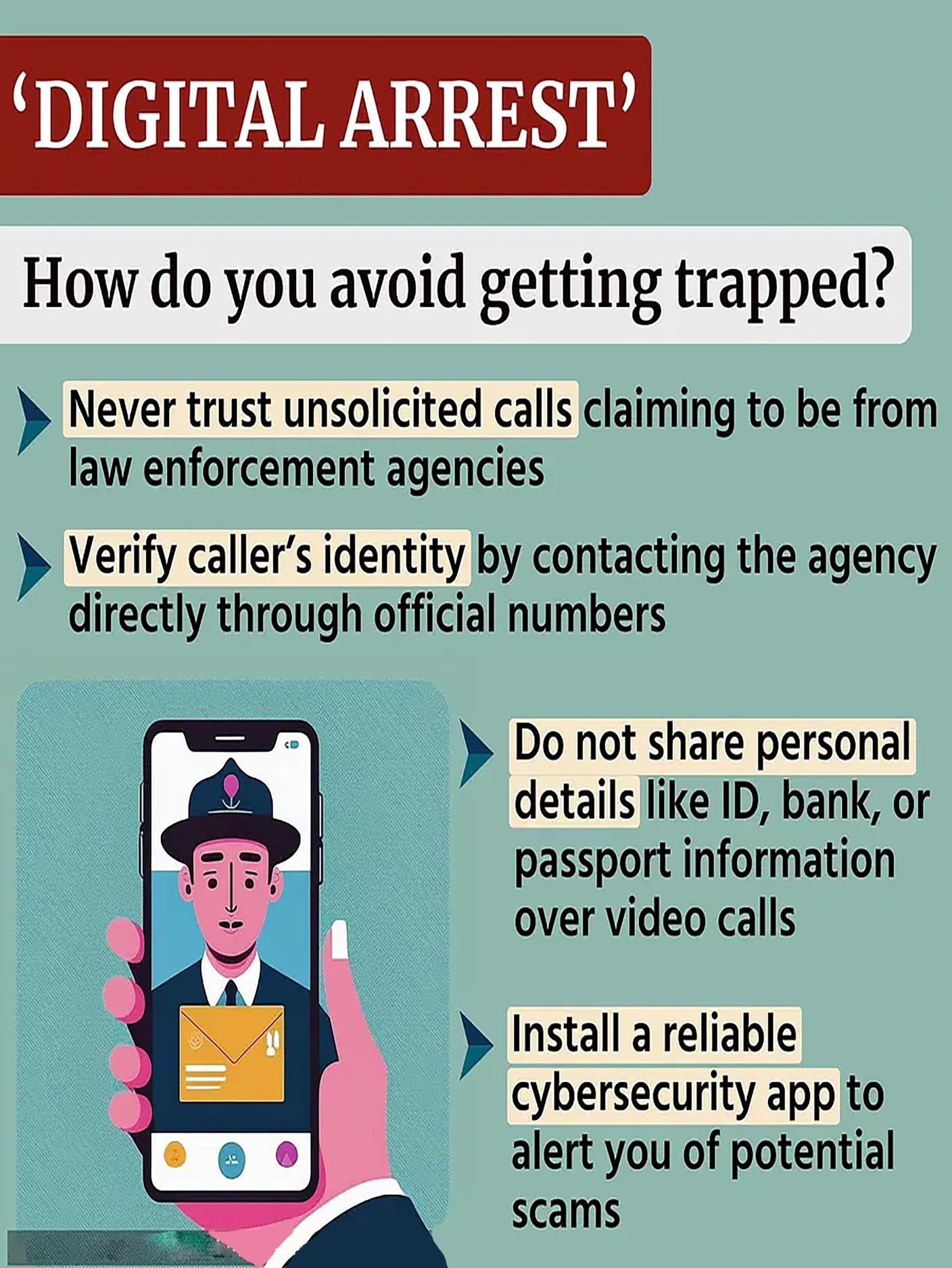
How to protect oneself from cybercrimes?
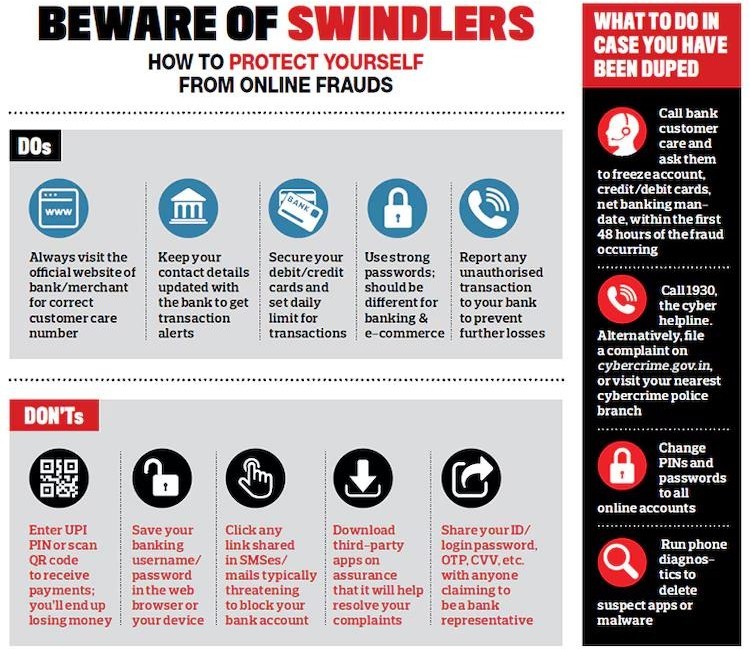
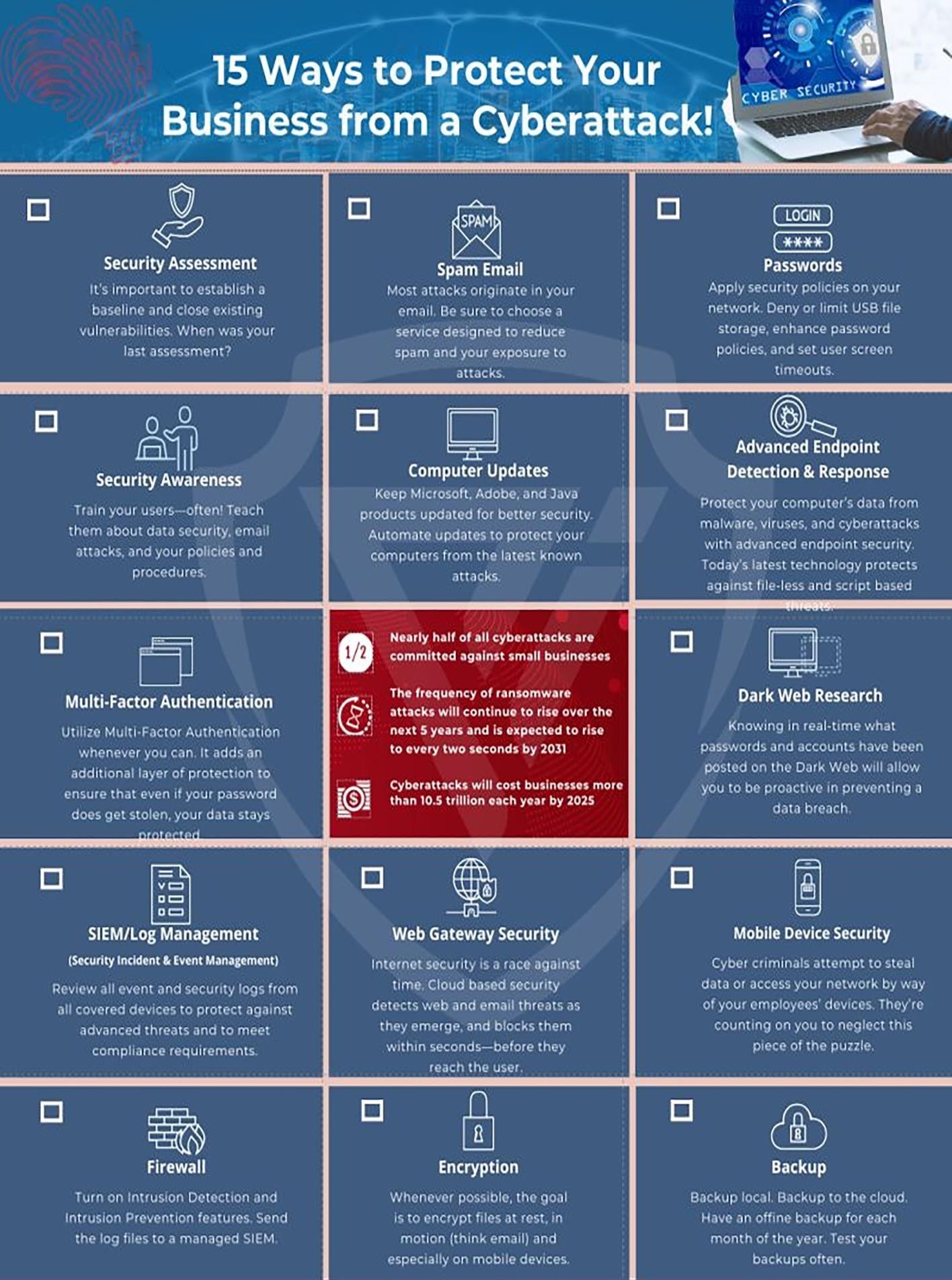
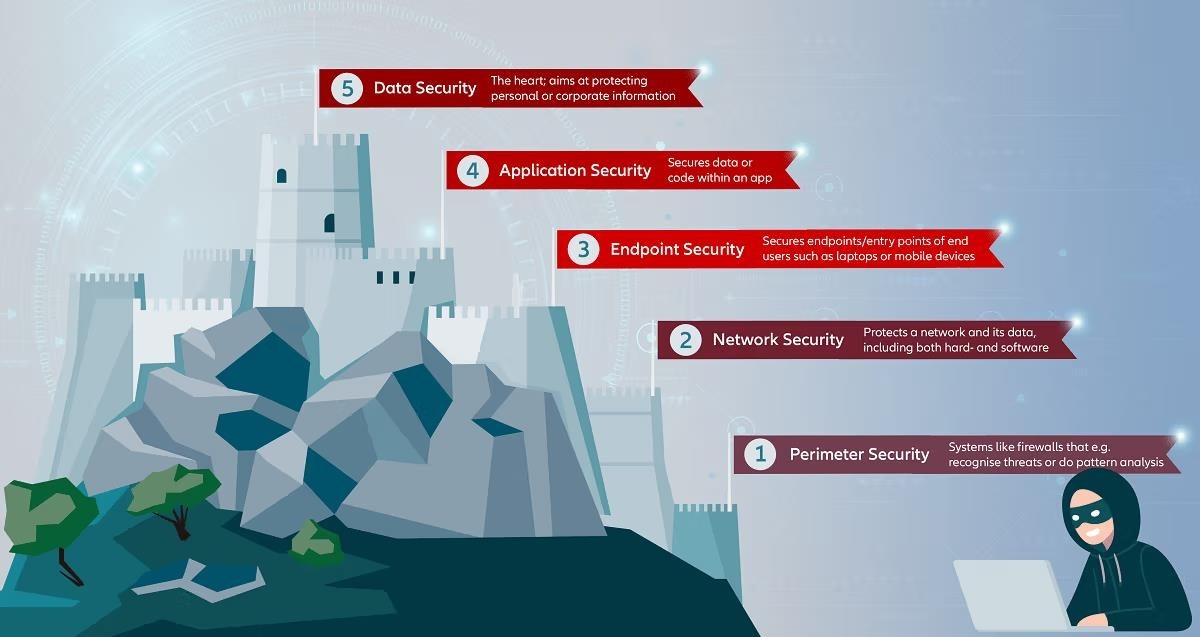
What is the relevance of the topic for UPSC CSE?
For Prelims: Cyber Crime, Seventh Schedule of the Constitution, Internet of Things, Crypto-Currency, Massive Open Online Courses.
For Mains: Internal security,Cyber Crime, Related Challenges and Measures to Deal with it.
Some Previous Years Prelims Questions
Q1. In India, under cyber insurance for individuals, which of the following benefits are generally, in addition to payment for the loss of funds and other benefits? (2020)
1. Cost of restoration of the computer system in case of malware disrupting access to a computer.
2. The cost of a new computer if some miscreant wilfully damages it, if proved so.
3. Cost of hiring a specialized consultant to minimize the loss in case of cyber extortion.
4. Cost of defense in the court of law if any third party files a suit.
Select the correct answer using the code given below:
(a) 1, 2, and 4 only
(b) 1, 3 and 4 only
(c) 2 and 3 only
(d) 1, 2, 3 and 4
Some Previous Years Mains Questions
Q1. Social media and encrypting messaging services pose a serious security challenge. What measures have been adopted at various levels to address the security implications of social media? Also suggest any other remedies to address the problem.[2024]
Q2. What is the status of digitalization in the Indian economy? Examine the problems faced in this regard and suggest improvements.[2023]
Q3. What are the different elements of cyber security? Keeping in view the challenges in cyber security, examine the extent to which India has successfully developed a comprehensive National Cyber Security Strategy. [2022]
Q4. Keeping in view India’s internal security, analyse the impact of cross-border cyber attacks. Also, discuss defensive measures against these sophisticated attacks. [2021]
Some Questions from This Year and Previous Years Interview Transcripts
Board B B Swain Sir:
- Does centralisation of web servers have risks?
- What type of cyber risks does it possess?
Board R N Choubey Sir:
- Cyber crimes are transnational, how to deal with them?
- How to prevent them?
Board Satyawati mam:
- Tell me something about cyber crimes
- Tell me something about social crimes and cyber crimes linkages
- How to prevent cyber crimes in India?
Board Preeti Sudan mam:
- What are cyber crimes?
- Mention a few examples of some cyber crimes?
- What steps need to be taken to tackle those crimes?
Some Questions for QUIZ
Q1. The term “zero-day exploit” closely relates to which of the following.
(a) Cyber attack
(b) Vehicular pollution
(c) Invasive Alien Species
(d) Cancer Drug Delivery
Some Questions for POLL
Q1. Do you think that rising cybercrime can hamper the Digital India mission?
(a) YES
(b) NO
(c) Can’t say
Q2. Should India be part of the UN cybercrime treaty?
(a) YES
(b) NO
(c) Can’t say
QUICK LINKS